Protecting User Data: Best Practices for Encryption in Android Development
Learn how to tackle common encryption challenge and discover best practices to ensure data security and user trust
In the modern digital age, where almost every interaction, transaction, and communication happens online, the importance of user data protection cannot be overstated. With billions of users entrusting their personal and sensitive information to various apps and platforms, developers are responsible for ensuring this data remains secure.
Encryption is the cornerstone for safeguarding user data. Essentially, it's the process of converting information into a code to prevent unauthorized access. For those working on the Android platform, mastering robust encryption techniques isn't just a best practice—it's an absolute necessity.
Being one of the most widely adopted platforms globally, Android is often in the crosshairs of malicious actors. As a result, those developing for Android must be proficient with the platform's security features and best practices. Prioritizing encryption ensures that user data remains shielded, even if an app or device is compromised.
Basics of Encryption
At its core, encryption is a method used to secure information by converting it into a code, making it unreadable to anyone without the appropriate decryption key.
In the realm of Android, with its vast user base and diverse range of applications, encryption plays a pivotal role in ensuring the confidentiality and integrity of data.
Types of Encryption
There are primarily two types of encryption methods:
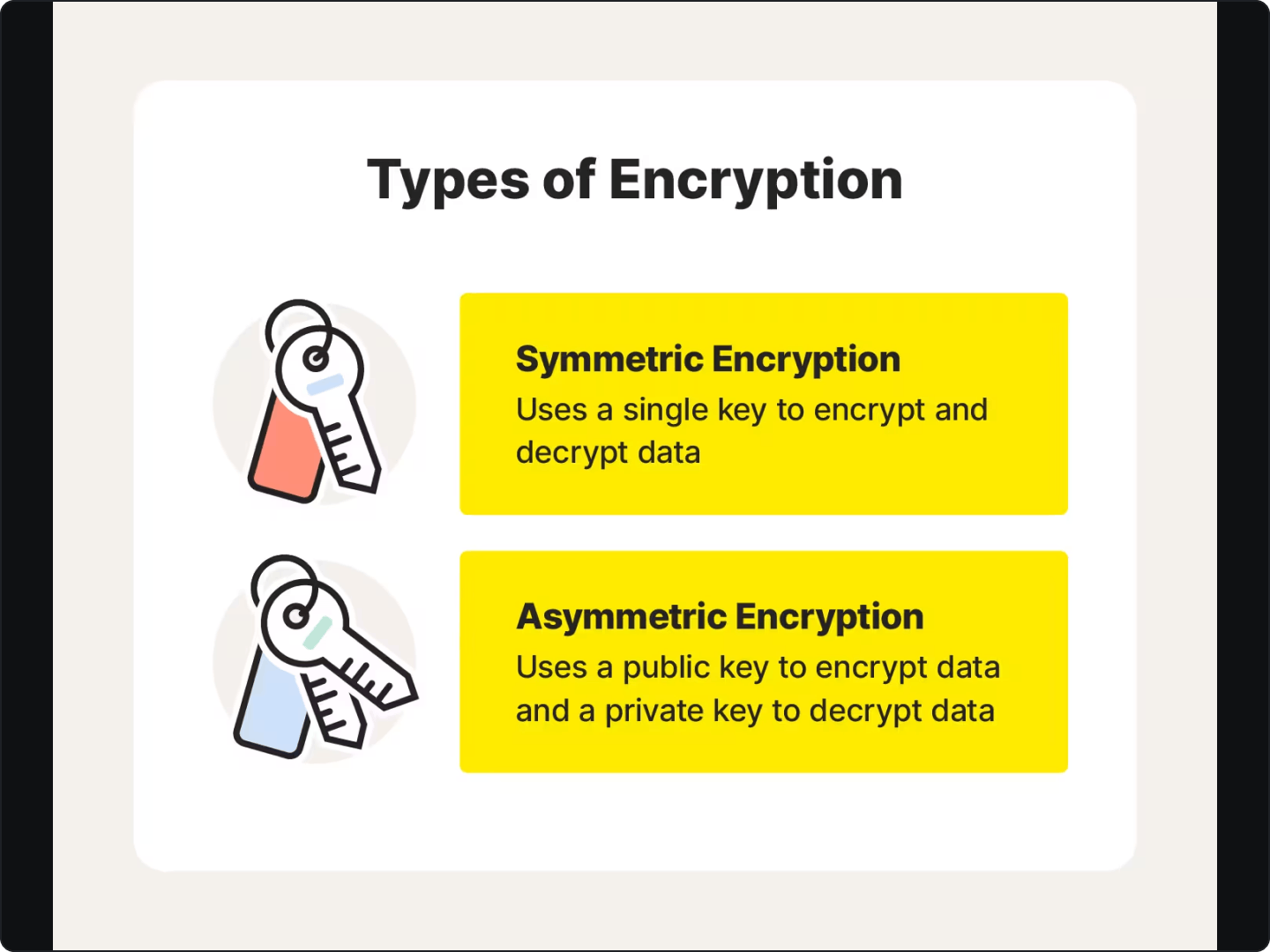
Symmetric Encryption: This involves a single key for both encryption and decryption. The most common symmetric encryption algorithm is AES (Advanced Encryption Standard). It's fast and efficient, making it suitable for encrypting large amounts of data.
Code example:
javaCopy codeimport javax.crypto.Cipher; import javax.crypto.spec.SecretKeySpec; byte[] key = "1234567890123456".getBytes(); // Example AES key SecretKeySpec secretKey = new SecretKeySpec(key, "AES"); Cipher cipher = Cipher.getInstance("AES"); cipher.init(Cipher.ENCRYPT_MODE, secretKey); byte[] encryptedData = cipher.doFinal("UserData".getBytes());Asymmetric Encryption: This involves a pair of keys: a public key for encryption and a private key for decryption. RSA (Rivest–Shamir–Adleman) is a widely used asymmetric encryption algorithm. It's more secure but slower than symmetric encryption, making it ideal for encrypting small amounts of data or for key exchange.
Code example:
javaCopy codeimport java.security.KeyPair; import java.security.KeyPairGenerator; import javax.crypto.Cipher; KeyPairGenerator keyGen = KeyPairGenerator.getInstance("RSA"); keyGen.initialize(2048); KeyPair keyPair = keyGen.generateKeyPair(); Cipher cipher = Cipher.getInstance("RSA"); cipher.init(Cipher.ENCRYPT_MODE, keyPair.getPublic()); byte[] encryptedData = cipher.doFinal("KeyData".getBytes());
Android's Built-in Security Features
The Android platform is designed with security at its core. Given its open-source nature and vast user base, Android has always been a prime target for malicious actors. Recognizing this, its creators have integrated a multi-layered security approach to ensure data protection and app integrity.
Keystore System
One of the most vital components in Android's security arsenal is the Android Keystore system. It provides a secure container, ensuring cryptographic keys are stored and managed safely, away from prying eyes. The Keystore system is especially crucial, as it offers a way to generate, store, and manage encryption keys without exposing them to potential threats.
Code example:
javaCopy codeimport android.security.keystore.KeyGenParameterSpec;
import android.security.keystore.KeyProperties;
KeyGenParameterSpec keySpec = new KeyGenParameterSpec.Builder(
"KeyAlias", KeyProperties.PURPOSE_ENCRYPT | KeyProperties.PURPOSE_DECRYPT)
.setBlockModes(KeyProperties.BLOCK_MODE_CBC)
.setEncryptionPaddings(KeyProperties.ENCRYPTION_PADDING_PKCS7)
.build();
KeyGenerator keyGenerator = KeyGenerator.getInstance(KeyProperties.KEY_ALGORITHM_AES, "AndroidKeyStore");
keyGenerator.init(keySpec);
SecretKey secretKey = keyGenerator.generateKey();
Hardware-backed Security
Android devices often come equipped with hardware-backed security features, such as the Trusted Execution Environment (TEE) and Hardware-backed Keystore.
These features ensure that sensitive operations, like key generation and cryptographic operations, are performed in an isolated, secure environment, making them resistant to software-based attacks.
Android Secure Element
Some Android devices also feature a Secure Element (SE), a tamper-resistant hardware component designed to securely store and process sensitive data, like payment credentials.
While not all apps will interact directly with the SE, knowing its capabilities can benefit working on security-critical applications.
Implementing Encryption
In the vast world of cryptography, selecting the appropriate encryption algorithm is paramount. While there are numerous algorithms available, not all are suitable for every scenario. For most Android applications, AES (Advanced Encryption Standard) stands out as the go-to symmetric encryption algorithm due to its balance of speed and security.
Advanced Encryption Standard
AES has become the industry standard for a reason. It offers robust security and is efficient for encrypting large datasets, making it ideal for Android applications handling user data.
Code example:
javaCopy codeimport javax.crypto.Cipher;
import javax.crypto.spec.SecretKeySpec;
byte[] key = "1234567890123456".getBytes(); // Example AES key
SecretKeySpec secretKey = new SecretKeySpec(key, "AES");
Cipher cipher = Cipher.getInstance("AES/CBC/PKCS7Padding");
cipher.init(Cipher.ENCRYPT_MODE, secretKey);
byte[] encryptedData = cipher.doFinal("UserData".getBytes());
Key Management
Generating and storing encryption keys securely is as crucial as the encryption process itself. Using the Android Keystore system, can ensure that encryption keys remain inaccessible to malicious actors.
Code example:
javaCopy codeimport android.security.keystore.KeyGenParameterSpec;
import android.security.keystore.KeyProperties;
KeyGenParameterSpec keySpec = new KeyGenParameterSpec.Builder(
"KeyAlias", KeyProperties.PURPOSE_ENCRYPT | KeyProperties.PURPOSE_DECRYPT)
.setBlockModes(KeyProperties.BLOCK_MODE_CBC)
.setEncryptionPaddings(KeyProperties.ENCRYPTION_PADDING_PKCS7)
.build();
KeyGenerator keyGenerator = KeyGenerator.getInstance(KeyProperties.KEY_ALGORITHM_AES, "AndroidKeyStore");
keyGenerator.init(keySpec);
SecretKey secretKey = keyGenerator.generateKey();
Utilizing Android's Encrypted File API
For storing files securely, Android offers the Encrypted File API. This API simplifies encrypting files, ensuring that data at rest remains protected.
Code example:
javaCopy codeimport androidx.security.crypto.EncryptedFile;
import androidx.security.crypto.MasterKeys;
String masterKeyAlias = MasterKeys.getOrCreate(MasterKeys.AES256_GCM_SPEC);
File file = new File(getFilesDir(), "encrypted_data.txt");
EncryptedFile encryptedFile = new EncryptedFile.Builder(
file,
this,
masterKeyAlias,
EncryptedFile.FileEncryptionScheme.AES256_GCM_HKDF_4KB
).build();
**
Common Mistakes**
Hardcoding Encryption Keys
One of the most frequent pitfalls to fall into is hardcoding encryption keys directly into the app's source code. While it might seem convenient, it's akin to leaving your house key under the doormat. Anyone accessing the app's code or who reverse engineers the APK can easily retrieve the key.
Code example (What NOT to do):
javaCopy codebyte[] key = "ThisIsABadIdea!".getBytes(); // Hardcoded key
Solution: Always generate encryption keys dynamically and store them securely, preferably using the Android Keystore system.
Neglecting to Update Cryptographic Libraries
Cryptography is a rapidly evolving field. What's considered secure today might be vulnerable tomorrow. Relying on outdated cryptographic libraries can expose apps to known vulnerabilities.
Solution: Regularly update cryptographic libraries and stay informed about the latest security advisories. Tools like Dependabot can be integrated into development workflows to detect and update outdated dependencies automatically.
Ignoring Side-Channel Attacks
While we often focus on direct attacks, side-channel attacks, which exploit information leaked during the encryption process, can be equally damaging. Examples include timing attacks or power analysis attacks.
Solution: Use constant-time algorithms that don't leak information through timing or power consumption. Regularly test and audit code for potential side-channel vulnerabilities. Familiarize yourself with common side-channel attacks to better defend against them.
Overlooking Proper Initialization Vector (IV) Management
Using a static or predictable Initialization Vector (IV) with encryption algorithms like AES can make the encryption predictable and vulnerable to attacks.
Code example (What NOT to do):
javaCopy codebyte[] iv = new byte[16]; // Static IV
Solution: Always generate a random IV for each encryption operation and store it securely. It's okay to store the IV alongside the ciphertext, as its purpose is to provide randomness, not secrecy.
Additional Security Measures
Biometric Authentication
In the age of digital innovation, passwords alone no longer suffice. Biometric authentication offers an added layer of security by leveraging unique physical or behavioral attributes, such as fingerprints or facial recognition.
Code example:
javaCopy codeimport androidx.biometric.BiometricPrompt;
import androidx.core.content.ContextCompat;
BiometricPrompt.PromptInfo promptInfo = new BiometricPrompt.PromptInfo.Builder()
.setTitle("Biometric Authentication")
.setSubtitle("Confirm your identity")
.setNegativeButtonText("Cancel")
.build();
BiometricPrompt biometricPrompt = new BiometricPrompt(this,
ContextCompat.getMainExecutor(this),
new BiometricPrompt.AuthenticationCallback() {
// Handle authentication callbacks here
});
biometricPrompt.authenticate(promptInfo);
Regular Code Audits
Periodically reviewing and auditing the app's codebase is essential. This proactive approach helps identify potential vulnerabilities or weak points before they can be exploited.
Solution: Employ tools like Android's Lint or third-party security scanners to automate the auditing process and ensure code quality.
Staying Updated
The Android platform is dynamic, with frequent updates and patches. Keeping the Android OS, SDK tools, and app dependencies up-to-date ensures you're protected against known vulnerabilities and can leverage the latest security enhancements.
Solution: Regularly check for updates on the Android Developers site and integrate tools like Dependabot to automate dependency updates.
Network Security
While encryption protects data at rest, securing data in transit is equally crucial. Implementing network security best practices, such as using HTTPS and validating SSL certificates, ensures data remains confidential and untampered during transmission.
Code example:
xmlCopy code<network-security-config>
<domain-config cleartextTrafficPermitted="false">
<domain includeSubdomains="true">secure.example.com</domain>
</domain-config>
</network-security-config>
FAQs
How can I ensure the encryption keys remain secure?
Avoid hardcoding keys; generate them dynamically.
Utilize the Android Keystore system for secure key storage and management.
How can I protect data during transmission?
Always use HTTPS for data transmission to ensure encrypted communication.
Ensure your app validates SSL certificates to prevent man-in-the-middle attacks.
Conclusion
In the world of Android development, innovation and user experience are paramount. However, the true cornerstone of any successful app lies in its security. Encryption and data protection aren't just technicalities; we make promises to our users, ensuring their data remains safe and their trust is upheld.
In this digital era, it's not just about creating apps but building trust. As we move forward, let's prioritize security, ensuring our users feel confident and protected every step of the way.

